Latest Insights & Articles
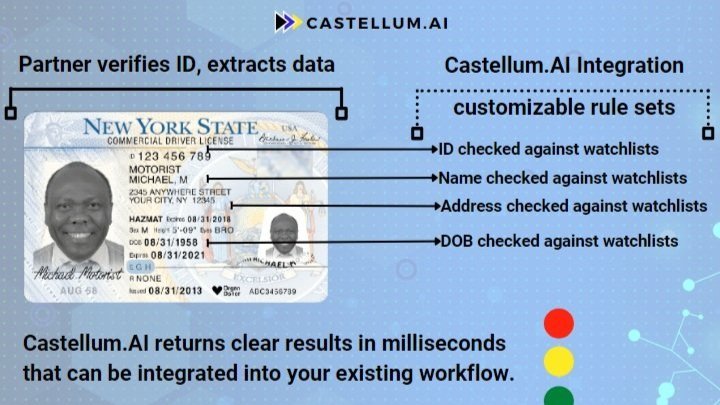
AML/KYC Data for Identity Verification
Identity Verification (IDV) is increasingly the first formal interaction users have with a business, sometimes even before providing their credit card number. This process is extremely difficult because the user expects it to be quick and frictionless, while the government expects it to be thorough and to check a number of legal requirements, including Knowing Your Customer (KYC). This becomes the first compliance check point for a business, and integrating watchlist checks into this step is crucial. After all, someone can have a valid ID, but still be on a terrorist watchlist.

How to Effectively Screen PEPs
Screening your customers and business counterparties to identify PEPs is an important part of a risk-based approach to AML compliance. Doing business with politically exposed persons is not prohibited, but organizations are mandated to identify PEPs and take appropriate measures to reduce money laundering risks.

KYC Screening for Financial Services
Discover the challenges and solutions in KYC screening for financial services. Explore how Castellum.AI enhances reliability, speed, and accuracy in compliance screening, reducing false positives and improving data quality.

Is Your Watchlist Data Any Good? We have a 5 minute test
We created a 5 minute test you can give to any compliance vendor to see if their data is any good. This this test is based on our experience as compliance technology users and purchasers in government and the private sector, as well as technology builders.
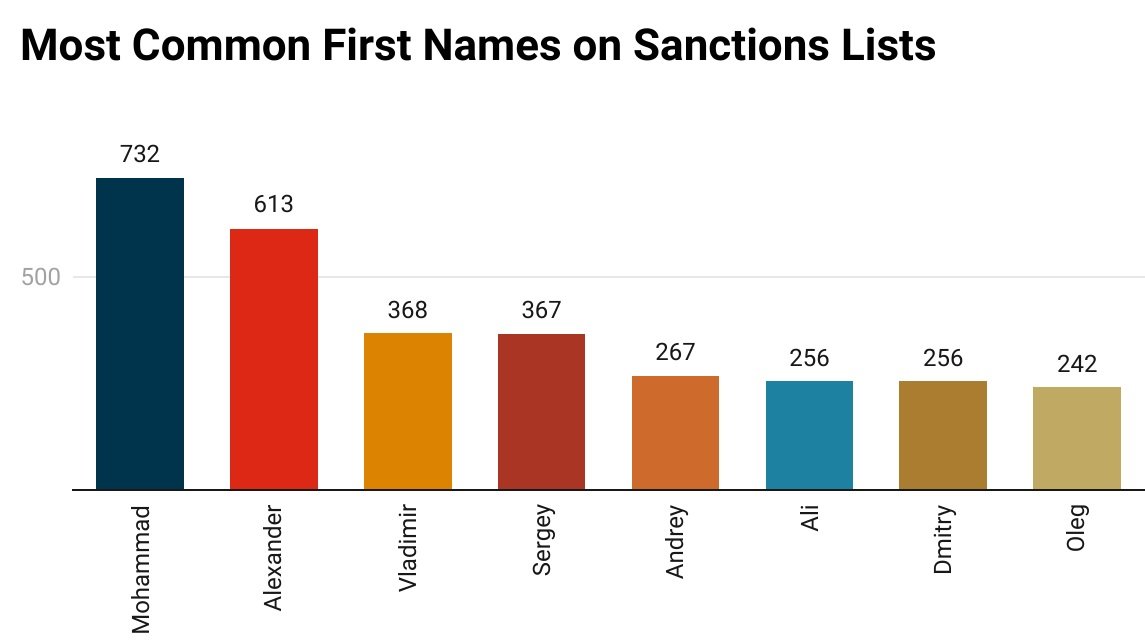
The Mohammad Bias: Watchlisting of Muslim Names
As of February 2023, the world’s most referenced sanctions authorities listed about 18,500 different individuals. Across this global data set, one name appears more than any other: Mohammad. This is despite the deluge of Russia-focused sanctions that began in March of 2022 after Russia’s invasion of Ukraine.

Supply Chain Compliance
Supply chain compliance refers to policies and procedures to ensure that a company’s suppliers and vendors are not subject to sanctions, export controls or other restrictions imposed by national laws. Violations of relevant restrictions can occur at any point in the supply chain, including the sourcing of raw materials, production, transportation or distribution of goods.

Announcing LIISA! Our Legal Identity Intelligent Suffix Adjudicator
Our new data enrichment process — LIISA — improves your ability to surface relevant watchlist results while minimizing false positives. By intelligently building context-based aliases otherwise absent from government watchlists, you can accurately search partial entity names.

Year in Review: 2022 Sanctions in 15 Charts
Sanctions globally grew significantly in 2022, with Russia dominating headlines. Meanwhile, sanctions targeting human rights abuses and corruption took center stage while targeted sanctions against Iran, Myanmar, and Belarus continued apace. The impact for 2023? Increased enforcement and fines as evasion efforts increase, sanctions on Iran are reinvigorated, and crypto sanctions become commonplace.

Ransomware Response and Sanctions Compliance
This step-by-step guide highlights exactly when sanctions compliance requirements are triggered during a ransomware attack. Ensuring that ransom payments are not directed to sanctioned actors, like REvil, enables incident response firms to avoid sanctions violations and cyber insurance providers to respond to claims.

How to Use the Global Sanctions Index in Country Risk Ratings
Learn how to use the Global Sanctions Index backing dataset to inform country risk ratings, identify sanctions compliance gaps across countries of operation, and identify which countries prioritize fighting financial crime.
